Serving our community since 2012
- Home
- Our Process
- Industries
- Resources
- Help Center
- Services
- Support
- Locations
- Service Area
- Contact Us
- About Us
- My Account
- Our Reviews
Home & Business Security Systems in Bellmore, NY
“Protecting Your Home & Business with Trusted Security Solutions.”
Keeping you safe & protected
We offer a diverse selection of top-tier security and home automation products and services tailored for both residential and commercial settings.
At CWC Security, we are dedicated to upholding the utmost standards in design, installation, and project management for security and communication systems. Our commitment includes comprehensive training programs for our staff to ensure they execute their tasks with safety and proficiency. Explore our extensive array of commercial and residential security solutions.
We will achieve continued business expansion by growing our client base and diversifying the services we offer. As our clients’ operations are positively impacted by our services, our business will prosper. Every aspect of CWC Security is designed to add value and deliver an urgent response to your changing needs with the right technology, custom-configured solutions, innovative extranet tools, technical expertise, specialized services and ongoing support.
Ensuring the safety and security of your premises is crucial in today's world. At CWC Security, we understand the importance of peace of mind when it comes to protecting what matters most to you.
As a leader in the alarm and security industry, we are committed to providing cutting-edge solutions tailored to your specific needs. With 30 years of expertise, our team specializes in designing, installing, and monitoring state-of-the-art security systems that offer comprehensive protection for residential and commercial spaces.
Legacy Payment - Client Portal
View work orders and quickly and securely pay your billing statements.
Log into My Customer Portal
All New Portal !!!
See service history, technician notes and more in your account.
- Home
- > Security Threat
Security Threat Assessment
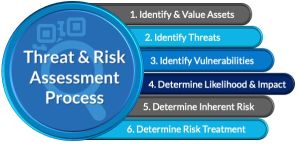 A security threat assessment is a process used to identify, evaluate, and prioritize potential threats to an organization's security, assets, or systems.
A security threat assessment is a process used to identify, evaluate, and prioritize potential threats to an organization's security, assets, or systems.
This process involves analyzing both internal and external vulnerabilities and determining the likelihood and potential impact of those threats.
The goal is to develop mitigation strategies to minimize or eliminate the identified risks.
Key aspects of a security threat assessment:
Evaluation:
Assessing the likelihood and potential impact of each identified threat.
Prioritization:
Ranking threats based on their potential impact and likelihood, allowing for focused resource allocation.
Mitigation:
Developing and implementing strategies to reduce or eliminate the identified risks.
Identification:
Recognizing potential threats, including malicious actors, natural disasters, or technical vulnerabilities.
Types of Threat Assessments:
Cybersecurity Threat Assessment:
.
Focuses on identifying threats to an organization's digital assets, networks, and systems.
Physical Security Threat Assessment:
.
Evaluates threats to physical infrastructure and personnel, such as access control and surveillance.
Behavioral Threat Assessment:
.
Analyzes potential threats from individuals, often in school or workplace settings, using a systematic process.
Importance of Security Threat Assessments:
Proactive Risk Management:
Helps organizations identify vulnerabilities and take preventative measures before a security incident occurs.
Resource Optimization:
Allows for efficient allocation of resources to address the most critical threats.
Compliance:
Ensures organizations meet industry regulations and standards related to security.
Incident Response:
Provides a framework for responding to security incidents and minimizing their impact.
